Integration News
B2B Integrator vulnerable to security bypass due to Apache Santuario XML
Security for Java
IBM Sterling B2B Integrator has addressed the secuirty vulnerabilities in Apache Santurio XML Security.
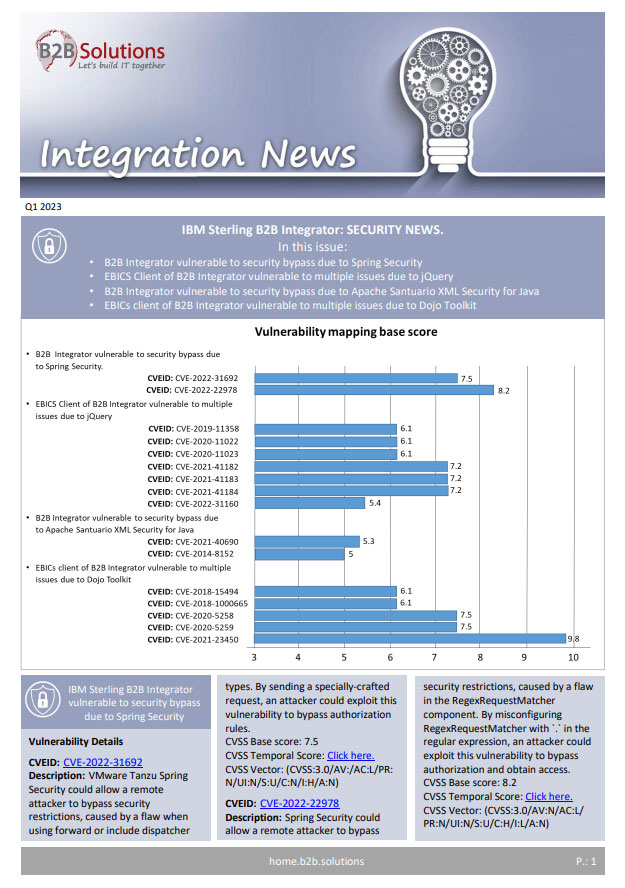
CVEID: CVE-2021-40690
Description: Apache Santuario XML Security for Java could allow a remote attacker to bypass security restrictions, caused by the improper passing of the “secureValidation” property when creating a KeyInfo from a KeyInfoReference element. An attacker could exploit this vulnerability to abuse an XPath Transform to extract any local .xml files in a RetrievalMethod element.
CVSS Base score: 5.3
CVSS Temporal Score: Click here.
CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
CVEID: CVE-2014-8152
Description: Apache Santuario XML Security for Java could allow a remote attacker to bypass security restrictions, caused by the failure to report an error when trying to validate the signature by the streaming XML Signature verification code. An attacker could exploit this vulnerability to modify a specific XML document.
CVSS Base score: 5
CVSS Temporal Score: Click here.
CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N)
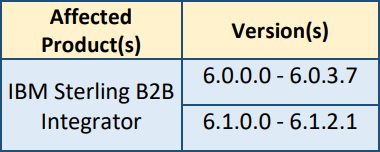
Affected Products and Versions
Remediation/Fixes

Workarounds and Mitigations
None.
The IIM versions of 6.0.3.8 and 6.1.2.2 are available on: Fix Central.
The container version of 6.1.2.2 is available in IBM Entitled Registry with following tags:
- icr.io/cp/ibm-b2bi/b2bi:6.1.2.2 for IBM Sterling B2B Integrator
- icr.io/cp/ibm-sfg/sfg:6.1.2.2 for IBM Sterling File Gateway