IBM Sterling Secure Proxy
Advanced edge security for your multi-enterprise data exchanges with high speed bridging and dynamic routing
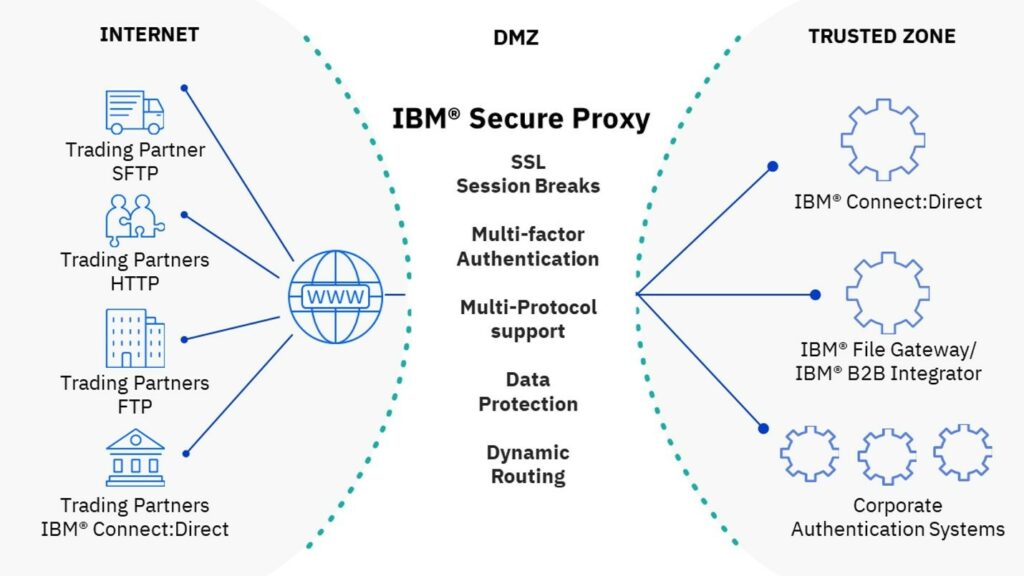
IBM Sterling Secure Proxy is a Demilitarized Zone (DMZ) application proxy that protects file transfers from the public Internet, imposing strict controls such as business partner authorization, multifactor authentication, and session interruption before the transfer get in the zone of trust.
IBM Sterling Secure Proxy provides you with a completely secure B2B file transfer.
Sterling Secure Proxy / SEAS Key Capabilities

The new dynamic routing capability empowers you to transparently migrate clients between different internal systems. It minimizes the risk of disruption during system migrations while avoiding external communication and coordination requirements. The real value is that it insulates your external trading partners and customers from your internal systems changes.
Dynamic routing allows internal system migrations to be performed transparent from external trading partners.
Keep files in good hands, with features that include:
Application proxy
- Resident in the demilitarized zone (DMZ)
- Supports IBM Connect:Direct servers, IBM Connect Express and IBM B2B Integrator
- Supports multiple DMZ environments
- Supports HSAO-FASP, FTP, FTPS, SCP, HTTP, HTTPS, AS2, SSH/SFTP, PeSIT and IBM Connect:Direct protocols
- Certified to run on most popular platforms including Linux, AIX, and Windows
- Integrates with existing directory services such as LDAP, Active Directory, and Tivoli
- Supports High speed add-on bridging
- Supports Dynamic Routing
- Includes a FIPS 140-2 compliant data encryption module with the option to force strict FIPS mode communications
Firewall navigation practices
- Prevents entry holes in the firewall
- Minimize key destinations in the demilitarized zone by ensuring that files, user credentials and data are not stored in the demilitarized zone
- Establish sessions from trusted areas to areas of lower confidence
- Enforces internal and external security policies
Perimeter security
- Prevents direct communications between internal and external sessions by
establishing secure session interruptions in the demilitarized zone via SSL or TLS - Inspect sensitive control information and protocol, enabling configurable error
handling for violations - Session limits and data encryption protect against denial of service attacks
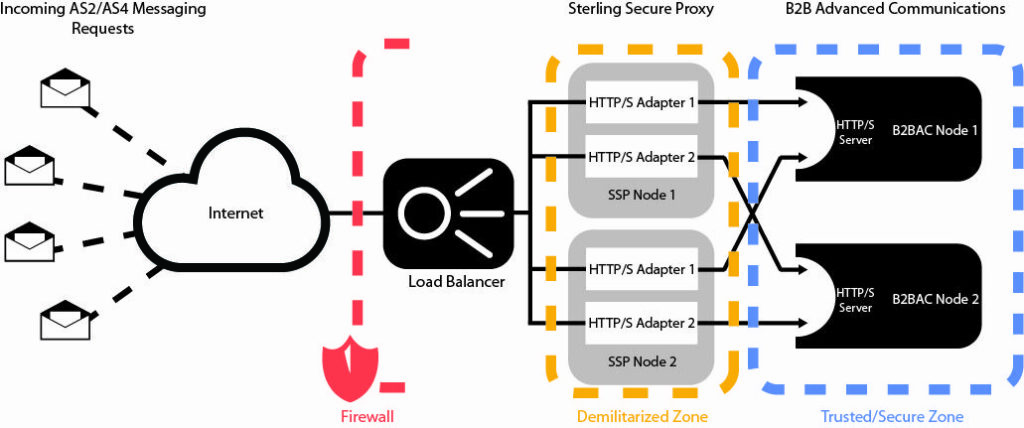
For a high availability deployment, you can install more than one IBM Sterling Secure Proxy node. In the following example, two IBM Sterling Secure Proxy nodes redirect requests to two B2B Advanced Communications nodes.
Authentication services
- The customizable login portal provides self-service password management for business partners
- Supports single sign-on and integrates with existing security infrastructure, including Active Directory and Tivoli user databases
- Multifactor authentication imposes severe controls and validation of business partner identity in DMZ before the information passes into the trusted zone
- Authentication options include the IP address, user ID and password, digital certificates, SSH Keys, RSA SecurID
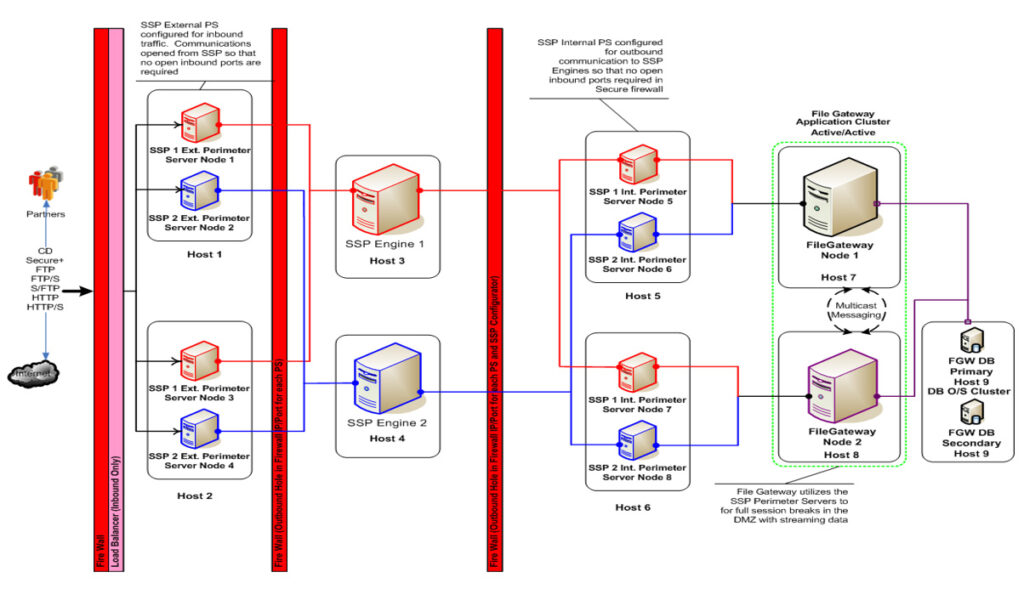
Clustering
- A central configuration manager directs configuration rules to several engines running in the demilitarized zone, facilitating the expansion
- Clustering for high availability and load balancing provides operational continuity and increased throughput
Contact B2B Solutions if you have questions or need more information about IBM Sterling Secure Proxy.


